Are you looking for an answer to the topic “Types Of Cryptography – Symmetric And Asymmetric Key Cryptography !!“? We answer all your questions at the website Chambazone.com in category: 40+ Marketing Blog Topics & Ideas. You will find the answer right below.
The most commonly used symmetric algorithms are AES-128, AES-192, and AES-256. The main drawback of the symmetric key encryption is that all individuals engaged in the activity have to exchange the key used to encrypt the data before they can decrypt it, which isn’t always convenient.Cryptography is broadly classified into two categories: Symmetric key Cryptography and Asymmetric key Cryptography (popularly known as public key cryptography). Now Symmetric key Cryptography is further categorized as Classical Cryptography and Modern Cryptography.
- Secret Key Cryptography.
- Public Key Cryptography.
- Hash Functions.
- Hash functions.
- Symmetric-key algorithms.
- Asymmetric-key algorithms.
- Hash Functions.
- Symmetric-Key Algorithms for Encryption and Decryption.
…
Difference Between Symmetric and Asymmetric Key Encryption.
| Symmetric Key Encryption | Asymmetric Key Encryption |
|---|---|
| Examples: 3DES, AES, DES and RC4 | Examples: Diffie-Hellman, ECC, El Gamal, DSA and RSA |
Table of Contents
Symmetric and Asymmetric Key Cryptography
Images related to the topicSymmetric and Asymmetric Key Cryptography
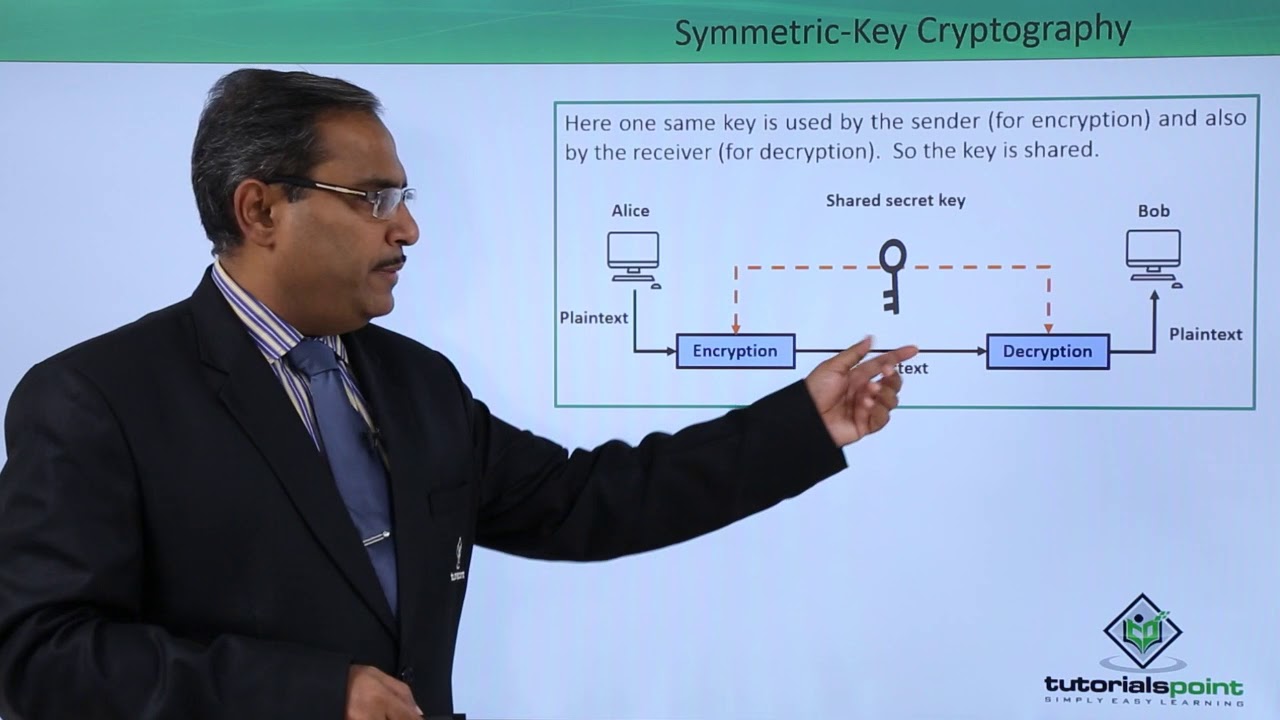
Security is an important aspect of the online world. Cybersecurity is based on cryptography. The word cryptography comes from Greek (meaning hden or secret). Cryptography is both the art and science of secretly writing information/messages and making them unreadable. The process of converting/converting a plaintext message to a ciphertext message is called encryption, and the process of converting/converting a ciphertext message to a plaintext message is called decryption. Cryptography can prove message confentiality, integrity, authentication, and non-repudiation. Cryptography is largely based on the principles of abstract algebra (although in this post we try to keep it largely theoretical). Simply put, in any encryption process, the initial plaintext is encrypted into ciphertext and finally converted back to plaintext through a decryption process at the receiving end. The original message is called plaintext before conversion. The converted message is called ciphertext. Encryption algorithms convert plaintext to ciphertext, and decryption algorithms convert ciphertext back to plaintext. The sender uses an encryption algorithm and the receiver uses a decryption algorithm. We can dive all cryptographic algorithms (passwords) into two groups: symmetric key (also known as secret key) cryptographic algorithms and asymmetric (also known as public key) cryptographic algorithms.
What Is Symmetric Key Cryptography ?
Symmetric key cryptography is also known as secret key cryptography or private key cryptography. Key encryption uses a single key for encryption and decryption. The encryption and decryption processes use the same key. It is expressed as P = D (K, E(P)). where P = plaintext, E(P) = plaintext encryption, D = decryption, and K = key. For example: stream ciphers and block ciphers. Data Encryption Standard (DES), Advanced Encryption Standard (AES), and BLOFISH. Since the same key is used for encryption and decryption, the recipient must possess the sender’s key, without which the recipient cannot decrypt (without the sender’s permission). A symmetric key satisfies the authentication principle because it verifies the entity of the recipient. DES and AES techniques are implemented using symmetric key encryption. Symmetric key encryption uses fewer system resources.
What Are Some Advantages & Disadvantages Of Symmetric Key Cryptography ?
Here are some benefits of symmetric encryption: Symmetric key encryption is faster than asymmetric key encryption. Because even if intercepted by an attacker, personal key data cannot be easily decrypted at the receiving end. Since the same key is used for encryption, and the recipient of decryption must have the sender’s key, they cannot decrypt without the sender’s permission. A symmetric key conforms to the principles of authentication because it verifies the entity of the recipient. Now some disadvantages of symmetric encryption: once the key is stolen while the data is being transferred between sender and receiver, since the same key is used for encryption and decryption, it is easy to decrypt the message. In symmetric key encryption, the key is transmitted first, and then the message is transmitted to the recipient. If an attacker intercepts the communication between the sender and receiver, they can decrypt the message before it reaches the intended recipient.
What Is Asymmetric Key Cryptography?
Asymmetric key cryptography is also known as public key cryptography or traditional cryptography. Asymmetric key encryption uses two keys, one for encryption and one for decryption. It is expressed as P = D(Kd, E(Ke,P)) where P = plaintext, E(P) = plaintext encryption, D = decryption, and Ke and Kd = encryption and decryption keys. For example: Rivest Shamir Adlman (RSA) and Diffie Hellman’s key exchange algorithm In public key encryption/decryption, the public key used for encryption is not the same as the private key used for decryption. The public key is available to the public and the private key is only available to a single recipient. Note: With symmetric key encryption, the same key can lock and unlock the box (message). With asymmetric key encryption, one key can lock the box, but another key is required to unlock it.
What Are Some Advantages & Disadvantages Of Asymmetric Key Cryptography ?
Some advantages of asymmetric key encryption can be seen: in asymmetric key encryption, the key cannot be distributed between the sender and the receiver, because both parties have their own keys, so the data is approximately 1 There are no key distribution issues when transmitting over insecure channels. The main advantage of asymmetric key encryption is the use of two separate keys for encryption and decryption; even if the encryption key is stolen by an attacker, he/she cannot decrypt the message because the decryption key is only available at the receiver. Now, some of the disadvantages of this type of cryptography are as follows: Different keys used between sender and receiver require more time to complete the transmission compared to symmetric key cryptography. (Slower than symmetric key cryptography, few asymmetric encryption schemes enable fast transfer of data). Asymmetric key encryption uses more resources than symmetric key encryption. Note: Please note that there are three types of keys used in cryptography, namely H. key (for symmetric encryption), we also have public and private keys for asymmetric encryption. I hope you really enjoyed this article on symmetric and asymmetric cryptography in cryptography. Stay tuned for more interesting content in this series. report this ad
What are the 2 types of cryptography?
- Secret Key Cryptography.
- Public Key Cryptography.
- Hash Functions.
What are the types of symmetric keys?
The most commonly used symmetric algorithms are AES-128, AES-192, and AES-256. The main drawback of the symmetric key encryption is that all individuals engaged in the activity have to exchange the key used to encrypt the data before they can decrypt it, which isn’t always convenient.
What are the types of cryptography?
Cryptography is broadly classified into two categories: Symmetric key Cryptography and Asymmetric key Cryptography (popularly known as public key cryptography). Now Symmetric key Cryptography is further categorized as Classical Cryptography and Modern Cryptography.
What are the 3 main types of cryptographic algorithms?
- Hash functions.
- Symmetric-key algorithms.
- Asymmetric-key algorithms.
- Hash Functions.
- Symmetric-Key Algorithms for Encryption and Decryption.
What is symmetric key in cryptography?
In cryptography, a symmetric key is one that is used both to encrypt and decrypt information. This means that to decrypt information, one must have the same key that was used to encrypt it.
What is asymmetric cipher?
Asymmetric cryptography, also known as public-key cryptography, is a process that uses a pair of related keys — one public key and one private key — to encrypt and decrypt a message and protect it from unauthorized access or use.
What are the types of asymmetric encryption?
- Rivest Shamir Adleman (RSA)
- the Digital Signature Standard (DSS), which incorporates the Digital Signature Algorithm (DSA)
- Elliptical Curve Cryptography (ECC)
- the Diffie-Hellman exchange method.
- TLS/SSL protocol.
What is symmetric cryptography and asymmetric cryptography?
Symmetric encryption uses a single key that needs to be shared among the people who need to receive the message while asymmetric encryption uses a pair of public key and a private key to encrypt and decrypt messages when communicating.
What is the difference between asymmetric and symmetric encryption?
Symmetric encryption uses a private key to encrypt and decrypt an encrypted email. Asymmetric encryption uses the public key of the recipient to encrypt the message. Then if the recipient wants to decrypt the message the recipient will have to use his/her private key to decrypt.
What are the differences among symmetric asymmetric and hashing algorithms?
The basic difference between these two types of encryption is that symmetric encryption uses one key for both encryption and decryption, and the asymmetric encryption uses public key for encryption and a private key for decryption.
Who is the father of cryptography?
Claude Shannon. Claude E. Shannon is considered by many to be the father of mathematical cryptography. Shannon worked for several years at Bell Labs, and during his time there, he produced an article entitled “A mathematical theory of cryptography”.
See some more details on the topic Types Of Cryptography – Symmetric And Asymmetric Key Cryptography !! here:
Symmetric And Asymmetric Key Cryptography – Jigsaw …
Symmetric encryption is an old technique. Asymmetric encryption is relatively new. RC4, AES, DES, 3DES, and other algorithms are examples. RSA, …
Symmetric vs. Asymmetric Encryption – What are differences?
Asymmetric encryption is also known as public key cryptography, which is a relatively new method, compared to symmetric encryption. Asymmetric encryption …
What is Cryptography? | Symmetric | Asymmetric | Hashing
Public Key Cryptography, or asymmetric cryptography, uses two keys to encrypt data. One is used for encryption, while the other key can decrypts the message.
Types of Encryption: Symmetric or Asymmetric? RSA or AES?
Encryption types can be easily dived into these two categories. Symmetric encryption, is single-key encryption, asymmetric encryption, or public-key …
Related searches to Types Of Cryptography – Symmetric And Asymmetric Key Cryptography !!
- compare some pros and cons of asymmetric key cryptography and symmetric key cryptography
- symmetric vs asymmetric encryption
- what are disadvantages of asymmetric key cryptography
- how confidentiality can be achieved using symmetric key and asymmetric key cipher
- symmetric and asymmetric
- Symmetric and asymmetric
- Symmetric key and asymmetric key
- Symmetric key Cryptography
- symmetric key cryptography
- Asymmetric encryption
- Symmetric vs asymmetric encryption
- Compare some pros and cons of asymmetric key cryptography and symmetric key cryptography
- asymmetric encryption
- symmetric key and asymmetric key
Information related to the topic Types Of Cryptography – Symmetric And Asymmetric Key Cryptography !!
Here are the search results of the thread Types Of Cryptography – Symmetric And Asymmetric Key Cryptography !! from Bing. You can read more if you want.
You have just come across an article on the topic Types Of Cryptography – Symmetric And Asymmetric Key Cryptography !!. If you found this article useful, please share it. Thank you very much.
