Are you looking for an answer to the topic “whitelist input validation“? We answer all your questions at the website Chambazone.com in category: Blog sharing the story of making money online. You will find the answer right below.
Whitelist validation is the practice of only accepting input that is known to be good. This can involve validating compliance with the expected type, length or size, numeric range, or other format standards before accepting the input for further processing.By whitelist you would define an input validator first, and only after that bind an input field to that validator. By a blacklist approach like this, it is easy to forget to add a validator to an input, and it works perfectly without that, so you would not notice the vulnerability, only when it is too late…Input validation, also known as data validation, is the proper testing of any input supplied by a user or application. Input validation prevents improperly formed data from entering an information system.
- 1: Data validation tool in Excel.
- 2: First level of data validation.
- 3: Second level of data validation.
- 4: Final level of data validation.

What is whitelist and blacklist validation?
By whitelist you would define an input validator first, and only after that bind an input field to that validator. By a blacklist approach like this, it is easy to forget to add a validator to an input, and it works perfectly without that, so you would not notice the vulnerability, only when it is too late…
What is proper input validation?
Input validation, also known as data validation, is the proper testing of any input supplied by a user or application. Input validation prevents improperly formed data from entering an information system.
26. Security Testing (Basics) – Blacklisting versus Whitelisting (Input Validation)
Images related to the topic26. Security Testing (Basics) – Blacklisting versus Whitelisting (Input Validation)

What are the four known data validation strategies?
- 1: Data validation tool in Excel.
- 2: First level of data validation.
- 3: Second level of data validation.
- 4: Final level of data validation.
What is input validation in SQL injection?
Input validation.
A common source of SQL injection is maliciously crafted external input. As such, it’s always a good practice to only accept approved input—an approach known as input validation. To protect against it, there are two variants of input validation: avoid list validation and preferlist validation.
What whitelisted means?
A whitelist (allowlist) is a cybersecurity strategy that approves a list of email addresses, IP addresses, domain names or applications, while denying all others.
What does whitelisted mean in data usage?
Your mobile hotspot is equipped with a whitelist function that will allow you to secure your network’s privacy. … When the primary user deactivates this feature, all other users will be allowed access to network via Wi-Fi and use of correct password.
Why is it not always possible to use a whitelist based approach to input validation?
Why is it not always possible to use a whitelist-based approach to input validation? There are many situations where an application may be forced to accept data for processing that does not match a list or pattern of input that is known to be “good”.
See some more details on the topic whitelist input validation here:
Input Validation – OWASP Cheat Sheet Series
Input validation is performed to ensure only properly formed data is entering the workflow in an information system, preventing malformed data from persisting …
C5: Validate All Inputs – OWASP Proactive Controls
Whitelisting or whitelist validation attempts to check that a given data matches a set of “known good” rules. For example a whitelist validation rule for a …
Input Validation – WhiteHat Security
While input validation can be either whitelisted or blacklisted, it is preferable to whitelist data. Whitelisting only passes expected data.
Input Validation · OWASP Cheat Sheet Series – DeteAct
White list validation is appropriate for all input fields provided by the user. White list validation involves defining exactly what IS authorized, …
What are the types of validation?
- A) Prospective validation (or premarket validation)
- B) Retrospective validation.
- C) Concurrent validation.
- D) Revalidation.
- A) Prospective validation.
Where should input validation occur?
Input Validation on Server-side
Server-side input validation will take whatever is sent by the client and conduct addition checks. Using server-side validation indicates that any input sent by the user (or client) cannot be trusted.
What are the 3 types of data validation?
Types of data validation include:
data range validation, code validation, and. data type validation.
Form validation – Phần 1
Images related to the topicForm validation – Phần 1
What are the 3 types of data validation in Excel?
- Any Value – no validation is performed. …
- Whole Number – only whole numbers are allowed. …
- Decimal – works like the whole number option, but allows decimal values. …
- List – only values from a predefined list are allowed. …
- Date – only dates are allowed. …
- Time – only times are allowed.
What are the validation techniques?
| Validation type | How it works |
|---|---|
| Length check | Checks the data isn’t too short or too long |
| Lookup table | Looks up acceptable values in a table |
| Presence check | Checks that data has been entered into a field |
| Range check | Checks that a value falls within the specified range |
What is input validation and output encoding?
Where Input Validation essentially says “I will only accept data that is obviously data”, Output Encoding says “I will only pass on data and code that can be told apart from each other”.
Why is it important to validate input in a script?
If the user provides the wrong number of inputs, or inputs of incorrect type or format, the script may generate an error, and/or behave oddly (and of course, you don’t like to see either of these results). For this reason, it is strongly recommended to spend some extra time writing code that validate user’s input.
Has can be used to validate the input?
Hash can be used to validate the input. Sometimes yes. >>Hash can be used to validate the input.
Why is IT called a whitelist?
A whitelist (or, less commonly, a passlist or allowlist) is a mechanism which explicitly allows some identified entities to access a particular privilege, service, mobility, or recognition i.e. it is a list of things allowed when everything is denied by default.
What is another word for whitelist?
Commonly Used Alternative Terms for Whitelist:
Allowlist and Acceptlist are the terms used in firewalls. We also have seen “Safelist” as an alternative for the term whiteliste. Another one we just heard recently is “welcome-list”. By the logic of not changing abbreviations, this term makes a lot of sense.
How does IP whitelisting work?
IP whitelisting is when you grant network access only to specific IP addresses. Each employee (or approved user) shares their home IP address with the network administrator, who then enters their IP address on a “whitelist” that grants them network access.
What is the best approach in regards of input validation?
Thus the best strategy for input validation is to use a combination of both a white list and a black list. Use a white list whenever possible; but when a meaningful white list is impractical, use a black list to block malicious input.
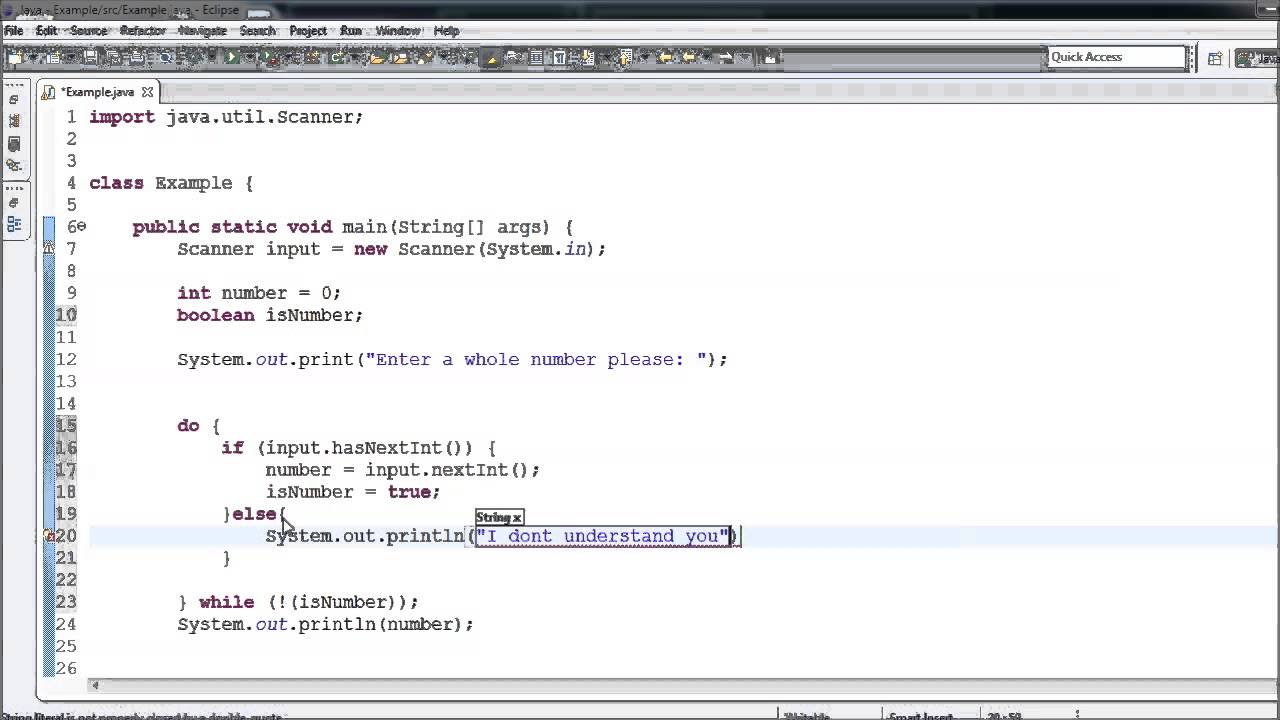
Java Tutorial – 11 – Validating User Input
Images related to the topicJava Tutorial – 11 – Validating User Input
Which is the most effective and secure way of handling user input?
Approaches based on data sanitization are often highly effective, and in many situations they can be relied upon as a general solution to the problem of malicious input.
How do you input validation in HTML?
The simplest HTML5 validation feature is the required attribute. To make an input mandatory, add this attribute to the element. When this attribute is set, the element matches the :required UI pseudo-class and the form won’t submit, displaying an error message on submission when the input is empty.
Related searches to whitelist input validation
- improper input validation
- input validation best practices
- use positive or whitelist server-side input validation
- whitelist vs blacklist input validation
- why is it not always possible to use a whitelist-based approach to input validation
- input validation vulnerability
- whitelist validation in java
- whitelist input validation in java
- whitelist input validation sql injection
- whitelist input validation filter
- whitelist input validation to protect against xss
- input validation javascript
- whitelist input validation example
- java classes used for whitelist input validation
- whitelist input validation means
- whitelist vs input validation
- whitelisting input validation
- input validation should be based on whitelisting or blacklisting
- input validation example
- whitelist input validation using regular expressions
- global whitelist input validation
- sql whitelist input validation
- whitelist input validation c#
Information related to the topic whitelist input validation
Here are the search results of the thread whitelist input validation from Bing. You can read more if you want.
You have just come across an article on the topic whitelist input validation. If you found this article useful, please share it. Thank you very much.
