Are you looking for an answer to the topic “why use prime number in hashcode“? We answer all your questions at the website Chambazone.com in category: Blog sharing the story of making money online. You will find the answer right below.
Constructing a good hash function, involves minimum number of collisions in the input sample, for a same number. So, using prime number reduces the count of collisions, since highly frequent number won’t have prime number as its multiple.Double hashing requires that the size of the hash table is a prime number. Using a prime number as the array size makes it impossible for any number to divide it evenly, so the probe sequence will eventually check every cell.The value 31 was chosen because it is an odd prime. If it were even and the multiplication overflowed, information would be lost, as multiplication by 2 is equivalent to shifting. The advantage of using a prime is less clear, but it is traditional.

Why prime number is used in double hashing?
Double hashing requires that the size of the hash table is a prime number. Using a prime number as the array size makes it impossible for any number to divide it evenly, so the probe sequence will eventually check every cell.
Why is 31 used in hashCode?
The value 31 was chosen because it is an odd prime. If it were even and the multiplication overflowed, information would be lost, as multiplication by 2 is equivalent to shifting. The advantage of using a prime is less clear, but it is traditional.
Why Prime Numbers are given much importance in writing certain algorithms like hashcode() in Java?
Images related to the topicWhy Prime Numbers are given much importance in writing certain algorithms like hashcode() in Java?

What makes a good hashCode?
hashCode values should be spread as evenly as possible over all ints. hashCode should be relatively quick to compute. hashCode must be deterministic (not random).
What is the purpose of the hashCode () method?
The purpose of the hashCode() method is to provide a numeric representation of an object’s contents so as to provide an alternate mechanism to loosely identify it. By default the hashCode() returns an integer that represents the internal memory address of the object.
Why is double hashing better than quadratic probing?
As the number of probes indicates the number of collisions, from the above table, linear probing has the highest number of probes followed by quadratic probing. Double hashing has the least number of probes hence minimum collisions. So, double hashing is the most efficient followed by quadratic probing.
Is double hashing more secure?
No, multiple hashes are not less secure; they are an essential part of secure password use. Iterating the hash increases the time it takes for an attacker to try each password in their list of candidates. You can easily increase the time it takes to attack a password from hours to years.
Can 2 objects have same hashCode?
It is perfectly legal for two objects to have the same hashcode. If two objects are equal (using the equals() method) then they have the same hashcode. If two objects are not equal then they cannot have the same hashcode.
See some more details on the topic why use prime number in hashcode here:
Why use a prime number in hashCode? – Stack Overflow
Prime numbers are chosen to best distribute data among hash buckets. If the distribution of inputs is random and evenly spread, …
[Solved] Why use a prime number in hashCode? | 9to5Answer
Because it’s an odd prime, and it’s “traditional” to use primes; It’s also one less than a power of two, which permits for bitwise optimization.
Why use a prime number in hashCode? – Genera Codice
Prime numbers are chosen to best distribute data among hash buckets. If the distribution of inputs is random and evenly spread, then the choice of the hash code …
Java – Why use a prime number in hashCode – iTecNote
Prime numbers are chosen to best distribute data among hash buckets. If the distribution of inputs is random and evenly spread, then the choice of the hash code …
Can hashCode return negative value?
Negative hashcode is perfectly valid!
It is perfectly legal to have negative hash codes, and if you are looking for hash values as used in hash-based collections you can use Math. abs(hash) . This can also give you negative numbers when hash is bigger than 2^31, and the best way would be to use a shift mask (key.
What is the importance of hashCode () and equals () methods?
The equals() and hashcode() are the two important methods provided by the Object class for comparing objects. Since the Object class is the parent class for all Java objects, hence all objects inherit the default implementation of these two methods.
Can 2 strings have same hashCode?
Two same strings/value must have the same hashcode, but the converse is not true. There might be another string which can match the same hash-code, so we can’t derive the key using hash-code. The reason for two different string to have the same hash-code is due to the collision.
What is the best strategy to calculate hashCode?
- Use a the same fields that are used in equals (or a subset thereof).
- Better not include mutable fields.
- Consider not calling hashCode on collections.
- Use a common algorithm unless patterns in input data counteract them.
Are Hashcodes unique?
They are not unique. Show activity on this post. By doing it’s own hashing of the key String, that code risks the chance that two different key strings will generate the same integer map key and the code will fail in some situations. In general, the code should probably be using Map<String,String> .
Understanding Java String Hashcode – explained with use cases and examples
Images related to the topicUnderstanding Java String Hashcode – explained with use cases and examples
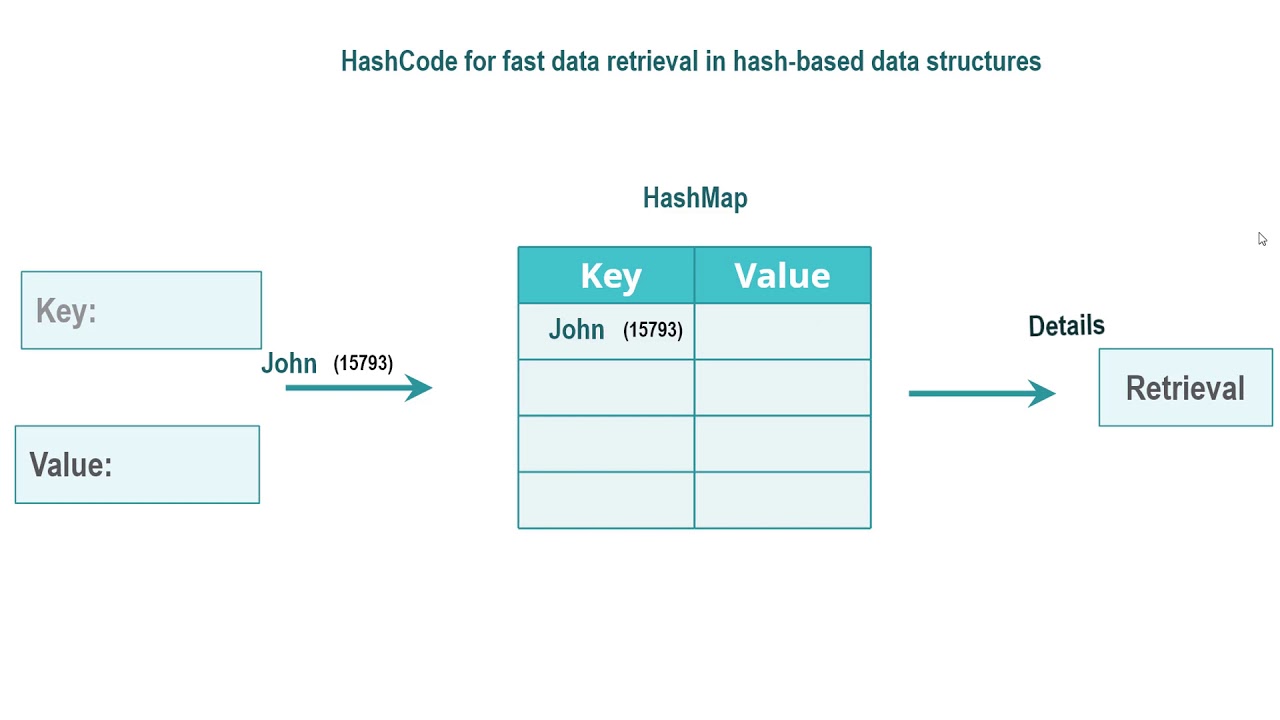
What is the difference between HashMap and Hashtable?
Hashmap vs Hashtable
It is thread-safe and can be shared with many threads. HashMap allows one null key and multiple null values whereas Hashtable doesn’t allow any null key or value. HashMap is generally preferred over HashTable if thread synchronization is not needed.
What is the return type of the hashCode ()?
Understanding How hashCode() Works
Simply put, hashCode() returns an integer value, generated by a hashing algorithm. Objects that are equal (according to their equals()) must return the same hash code.
What is a hash string?
Hashing is the process of transforming any given key or a string of characters into another value. This is usually represented by a shorter, fixed-length value or key that represents and makes it easier to find or employ the original string. The most popular use for hashing is the implementation of hash tables.
What is difference between open hashing and closed hashing?
Open Hashing (Separate Chaining): In open hashing, keys are stored in linked lists attached to cells of a hash table. Closed Hashing (Open Addressing): In closed hashing, all keys are stored in the hash table itself without the use of linked lists.
How hash tables grow and shrink?
The usable size of a hash table is the number of associations that the table can hold at a given time. If the number of associations in the table exceeds the usable size, the table will automatically grow, increasing the usable size to a new value that is sufficient to hold the associations.
What is the difference between linear probing and quadratic probing?
Linear Probing has the best cache performance but suffers from clustering. Quadratic probing lies between the two in terms of cache performance and clustering. Double caching has poor cache performance but no clustering.
What is the most secure hash?
Common attacks like brute force attacks can take years or even decades to crack the hash digest, so SHA-2 is considered the most secure hash algorithm.
What is Hmac in security?
Hash-based Message Authentication Code (HMAC) is a message authentication code that uses a cryptographic key in conjunction with a hash function. Hash-based message authentication code (HMAC) provides the server and the client each with a private key that is known only to that specific server and that specific client.
What is double hashing example?
Double Hash Function
The first hash function determines the initial location to located the key and the second hash function is to determine the size of the jumps in the probe sequence. The following function is an example of double hashing: h(key, i) = (firstHashfunction(key) + i * secondHashFunction(key)) % tableSize.
What happens if hashCode returns constant?
Returns the same hash code for the given object as would be returned by the default method hashCode(), whether or not the given object’s class overrides hashCode(). The hash code for the null reference is zero. So even if the hashcode() is overridden, it should not effect it.
Java interview question on hashcode() and equals() || Java collection interview questions on HASHMAP
Images related to the topicJava interview question on hashcode() and equals() || Java collection interview questions on HASHMAP
What happens if we do not override hashCode () and equals () in HashMap?
You must override hashCode in every class that overrides equals. Failure to do so will result in a violation of the general contract for Object. hashCode, which will prevent your class from functioning properly in conjunction with all hash-based collections, including HashMap, HashSet, and Hashtable.
What happens if hashCode returns same value?
If multiple objects return the same value from hashCode(), it means that they would be stored in the same bucket. If many objects are stored in the same bucket it means that on average it requires more comparison operations to look up a given object.
Related searches to why use prime number in hashcode
- java string hashcode implementation
- hash code prime number
- java hash
- java hashcode calculator
- is 4913 a prime number
- why prime number is used in hashing
- why are prime numbers important in cryptography
- why we use prime number in hashcode
- java hashcode
- Hash code prime number
- why use 31 in hashcode
- java override hashcode best practice
- why prime numbers are used in cryptography
- is a number prime algorithm
- best prime number for hashing
- what is a prime square number
- hashcode prime number
- primes for hashing
- why does cryptography use prime numbers
- sha256 prime numbers
Information related to the topic why use prime number in hashcode
Here are the search results of the thread why use prime number in hashcode from Bing. You can read more if you want.
You have just come across an article on the topic why use prime number in hashcode. If you found this article useful, please share it. Thank you very much.
